How to Secure Your Web App: Essential Security Practices for 2025
Nauman Pathan
April 14, 2025 22 Views
Quick Summary : Securing your web application in 2025 calls for a proactive and non-stop approach. From planning and development to deployment and up-launch tracking, web app security should be included at each stage. Emphasising steady coding, using relied-on frameworks, validating in opposition to the OWASP Top 10, and participating with a reliable custom web app development company is key. Adopting those vital security practices facilitates decreasing vulnerabilities, defends user information, and builds trust for a lengthy period. Whether learning to build web app capabilities securely or strengthening a current product, a “shift-left” mindset guarantees stronger protection in an ever-evolving virtual danger landscape.
Nowadays, web app security is no longer compulsory in a virtual world – this is important. With a steady increase in cyber attacks, businesses dependent on digital structures should act as strong safety practices for their data, infrastructure and the safety of users. Whether running with a custom web app development company or building your answer in-house, securing your app from design to deployment is key. This guide walks you through the critical safety practices for 2025 and beyond.
Why Web App Security Matters More Than Ever
Every click, form submission, and data exchange in your web app can be a potential entry point for attackers. The shift to remote work, cloud platforms, and increased API integration has exposed new vulnerabilities. And customers today expect secure digital experiences. One breach can damage your reputation, cost millions, and lose customer trust.
That’s why investing in web app security is both a defensive and strategic move.
Understanding the Importance of Web App Security
A weak web application can cause data violations, financial loss and iconic damage. Cybercriminals often use poorly coded apps, misunderstanding servers or old software. As a result, it’s critical to implement industry-standard procedures and match your tactics to the top 10 security threats identified by Owasp.
Web app security guarantees that your apps manage data sensibly, successfully authenticate users and preserve the integrity of the systems they communicate with. This user also creates trust and helps meet compliance standards such as GDPR, HIPAA and PCI-DSS.
Top 10 Open Web Application Security Projects
The OWASP Top 10 globally recognised framework highlights the most critical web application security risks. Staying updated with the Open Web Application Security Project’s annual changes is fundamental to securing your app. Here are the top threats from the Open Web Application Security Project Top 10:
- Broken Access Control – Unauthorized users gaining access to restricted resources.
- Cryptographic Failures – Weak or missing encryption.
- Injection – Attackers injecting malicious code, especially SQL.
- Insecure Design – Poor architectural choices that create security loopholes.
- Security Misconfiguration – Incorrect settings that open your app to attack.
- Vulnerable Components – Using outdated libraries or plugins.
- Identification & Authentication Failures – Login system flaws.
- Software & Data Integrity Failures – Issues with updates or plugins.
- Security Logging & Monitoring Failures – Missed detection of security breaches.
- Server-Side Request Forgery (SSRF) – Attackers trick the server into accessing internal resources.
Your online application will be safe if your safety roadmap owes the top 10. These weaknesses can be found and fixed before they are exploited with the help of regular audits based on the Owasp top 10.
Secure Coding Tips: Building with Security in Mind
Secure coding is non-negotiable if you’re exploring how to build web app projects safely. Here are vital secure coding tips every developer and architect should adopt:
- Input Validation: Sanitize and validate all user input to prevent injection attacks.
- Use HTTPS Everywhere: Encrypt all data in transit.
- Authentication Best Practices: Enforce strong password policies and multi-factor authentication (MFA).
- Access Control: Implement least privilege and role-based access controls.
- Avoid Hardcoding Secrets: Use environment variables or secure secret management tools.
- Error Handling: Don’t expose stack traces or sensitive error messages to end-users.
Implementing these coding principles early in your software development lifecycle helps reduce vulnerabilities downstream.
Choosing a Custom Web App Development Company
Security begins with design. Partnering with a trustworthy custom web app development company ensures security is embedded from the ground up. Here’s what to look for:
- A company that follows security-first architecture
- Experienced in compliance (like GDPR, HIPAA, PCI-DSS)
- Delivers regular code reviews and penetration testing
- Incorporates DevSecOps practices
Choosing a partner who understands how to build progressive web app systems securely saves time, avoids costly refactors, and ensures peace of mind.
Best Practices for Web Application Security in 2025
Web app threats evolve fast. Here’s what’s trending and essential in 2025:
1. Zero Trust Architecture
A “Never trust, always verify” model. Each internal or external request must be certified, authorised and constantly valid, ensuring that users and equipment have the correct access and intention.
2. DevSecOps Integration
Embed security during your software development life cycle. Integrate devices such as SAST, DAST and container scanning in CI/CD pipelines to identify weaknesses without slowing down the development workflow.
3. API Security
Secure APIs using API gateways, OAuth tokens, rate limiting, and input validation. Monitor for misuse and prevent exposure of sensitive data via robust authentication and endpoint control mechanisms.
4. Real-Time Monitoring and Incident Response
Deploy SIEM systems to identify abnormal patterns instantly. Pair this with a documented, regularly tested incident response plan to react fast to breaches or unusual behaviours.
5. Supply Chain Risk Management
Assess third-party libraries and frameworks rigorously. To guarantee openness, version control, and prompt patching of any vulnerabilities, keep an extensive Software Bill of Materials (SBOM).
6. AI-Driven Threat Detection
Leverage machine learning and AI to present suspicious behaviour and emerging hazards. These systems develop continuously, which helps you to be refined and ahead of zero-day cyber attacks.
7. Make use of MFA (multi-factor authentication).
MFA significantly reduces account compromise risks. Combine passwords with SMS, biometric, or hardware tokens—especially for users with privileged access or sensitive data visibility.
8. Implement Content Security Policy (CSP)
CSP controls which scripts and content a browser can execute. Limiting resource origins lowers the danger of code injection, clickjacking, and Cross-Site Scripting (XSS) attacks.
9. Data Encryption
Always encrypt data into comfort and transit using standards such as TLS 1.3. It protects sensitive user information, even if the data has been intercepted or unfairly accessed.
10. Automate Security Testing
Incorporate tools for static, dynamic, and dependency analysis. Automated testing catches flaws early, making remediation easier and ensuring continuous security checks throughout development.
11. Regular Penetration Testing
Hire ethical hackers to simulate real-world attacks. Pen tests reveal hidden or overlooked security gaps, offering actionable insights to strengthen your application’s defence layers.
12. Keep Dependencies Updated
Outdated components are common attack vectors. Use automated dependency managers and vulnerability scanners to regularly patch, upgrade, or replace insecure packages.
13. Access Logging and Monitoring
Record all user and system access activities. Examine logs for trends, look at irregularities, and create alerts for any questionable activity that might point to a breach.
14. Train Your Team
Security is a shared responsibility. Educate developers, QA testers, and non-tech teams about phishing, password hygiene, secure coding, and other essential practices through ongoing training sessions.
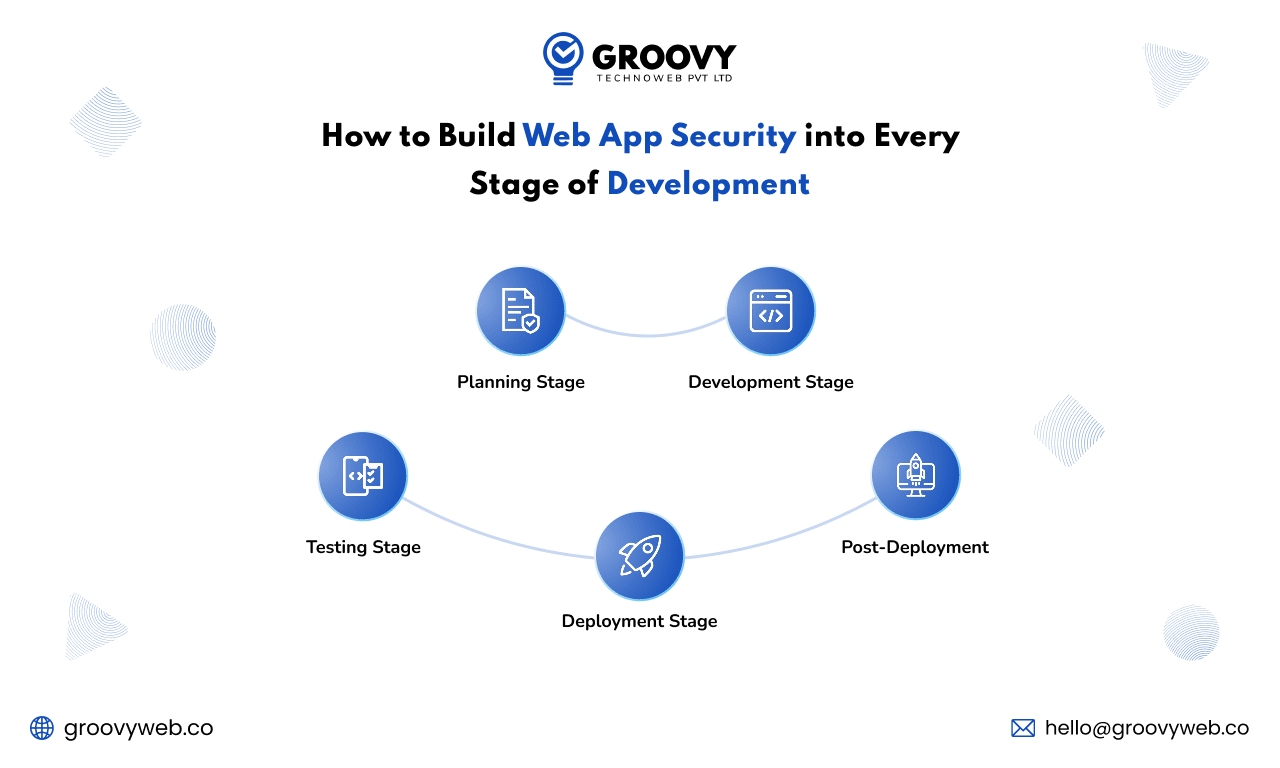
How to Build Web App Security into Every Stage of Development
Security isn’t just a QA checklist item. It’s a culture. Here’s how to build it into your software development lifecycle:
1. Planning Stage
Establishing security early helps prevent costly fixes later. Define precise security goals, perform threat modelling, and align stakeholders to ensure vulnerabilities are identified before writing any code.
Define security requirements
Set clear security expectations for authentication, data protection, and compliance before development begins.
Include threat modeling
Identify and assess potential threats by mapping data flow and attack surfaces.
2. Development Stage
Make sure that every line of code incorporates security. Developers must adhere to safe procedures and use reliable technologies to create a robust app that resists contemporary cyberattacks.
Follow secure coding tips.
Write code that prevents common vulnerabilities like injection and data exposure.
Use secure frameworks and libraries.
Select maintained, security-focused libraries and avoid outdated or risky dependencies.
3. Testing Stage
Security testing should be rigorous and frequent. Combine automated scans with expert-driven manual testing to cover code-level and business logic vulnerabilities.
Run automated and manual security tests.
Use a mix of tools and human review to find and fix vulnerabilities.
Validate against the Open Web Application Security Project Top 10
Test your app against the most critical known security risks.
4. Deployment Stage
Security doesn’t stop after coding. Infrastructure and deployment pipelines must be hardened to prevent configuration drift and unauthorised changes.
Review infrastructure configuration
Double-check server, network, and cloud settings for potential weaknesses.
Use automated CI/CD with built-in security checks.
Integrate security into every deployment to catch issues before they reach production.
5. Post-Deployment
An app is only as secure as its last update. Ongoing vigilance helps protect against zero-day threats and evolving attack techniques.
Monitor logs
Track and analyse activity logs for unusual or malicious behaviour.
Apply patches regularly
Keep systems and libraries updated to reduce exploit risk.
This “shift-left” security mindset can help mitigate risks early and reduce time-to-fix.
Role of Custom Web App Development Companies
A custom web app development company brings experience and industry-specific insights that help in safe applications from the ground. Whether you are building for Fintech, Healthcare, or Retail, experienced developers understand specific compliance and safety nuances for each field.
Such companies often appoint moral hackers and cyber security professionals who perform vulnerability assessments and admission tests. When outsourcing, ensure that the company follows strict security protocols, maintains the code version, and distributes documents for ongoing maintenance.
Security Tools Every Developer Should Know
These resources can be useful if you’re trying to figure out how to create web app projects safely:
- Burp Suite: For vulnerability scanning and penetration testing.
- OWASP ZAP: An open-source program for identifying security flaws.
- SonarQube: Examines the quality of the code and identifies security flaws.
- io: Looks for vulnerabilities in online apps and infrastructure.
- HashiCorp Vault: Keeps secrets safe and organised.
During the development and testing stages, these technologies assist developers in automating vulnerability identification and mitigation.
Common Mistakes That Compromise Web App Security
Avoid these pitfalls to keep your application secure:
- Ignoring security in the early development stages
- Delayed software updates or ignoring patches
- Using default credentials or weak authentication
- Inadequate encryption of sensitive data
- Poor logging and monitoring practices
Being proactive instead of reactive is key to avoiding these mistakes.
Compliance Considerations
Security isn’t just a best practice—it’s often a legal requirement. Depending on your industry, your application might need to comply with:
- GDPR: This is for handling EU citizens’ user data.
- HIPAA: For healthcare-related apps in the US.
- PCI DSS: For handling payment information.
- ISO/IEC 27001: For information security management systems.
A business that develops custom web apps can assist you in navigating these legal constraints and include compliance in your design and implementation process.
The Human Element in Web App Security
Even the most secure codebase can be compromised by human error. Train your development, DevOps, and support teams regularly. Educate your customers about phishing attacks and enforce good security.
Security is a shared responsibility—it requires awareness and vigilance across your organisation.
Trends to Watch in Web App Security for 2025
1. AI-Assisted Threat Detection
AI tools are being used to predict and detect new threats before they happen.
2. Cloud-Native Security
Integrating cloud-specific security tools is crucial with more apps hosted on cloud platforms.
3. DevSecOps
Security as part of development pipelines (DevOps + Security) is now necessary.
4. Privacy-First Design
Security isn’t just about hackers—it’s also about user data protection.
5. Automation of Compliance
Regulations are increasing. Automating compliance reports helps you stay audit-ready. These trends are redefining web app security and how modern teams stay protected.
Final Thoughts
Securing your web app in 2025 is not just blocking intrusion but designing your users’ trusting experiences. Whether coding from scratch or trusting the custom web app development company, remember that security should be a priority. From following Owasp Top 10 to embedding safe coding tips in its workflow, the key is active, notified, and always one step forward. Looking to take your web app to the next level? It all starts with a safe foundation.
Written by: Nauman Pathan
Nauman Pathan is a Project Manager at Groovy Web - a top mobile & web app development company. He is actively growing, learning new things, and adapting to new roles and responsibilities at every step. Aside from being a web app developer, he is highly admired for his project management skills by his clients.
Frequently Asked Questions
We hope these clear your doubts, but if you still have any questions, then feel free to write us on hello@groovyweb.coWhy is cybersecurity important for startups?
Cybersecurity protects startups from data breaches and cyberattacks, which can result in financial losses and reputational damage. By implementing robust security measures like encryption, firewalls, and multi-factor authentication, startups can safeguard sensitive data and maintain customer trust.
How does CRM software help startups scale?
CRM software centralizes customer data and automates sales processes, allowing startups to improve customer relationships, track leads efficiently, and automate marketing campaigns. It helps scale operations by enhancing customer engagement, streamlining workflows, and providing valuable insights for growth.
What role do AI and automation play in startup growth?
AI and automation streamline repetitive tasks, improve decision-making, and enhance customer experiences. By automating processes like marketing, chat support, and workflows, startups can boost efficiency, reduce costs, and focus on strategic activities, fostering faster scalability and growth.
How does scalable web and app development benefit startups?
Scalable web and app development ensures applications can handle increasing traffic and users without performance issues. Using frameworks like MERN Stack and adopting cloud-native architectures allows startups to grow efficiently, ensuring seamless user experiences and adaptable business solutions.
Related Blog

Rahul Motwani
How Document Management Systems Improve Workflow and Productivity
Mobile App Development 18 Dec 2024 10 min read
Ashok Sachdev
ASP.NET vs PHP - What to Choose for Your App Needs
Web App Development 14 Nov 2024 8 min readSign up for the free Newsletter
For exclusive strategies not found on the blog
